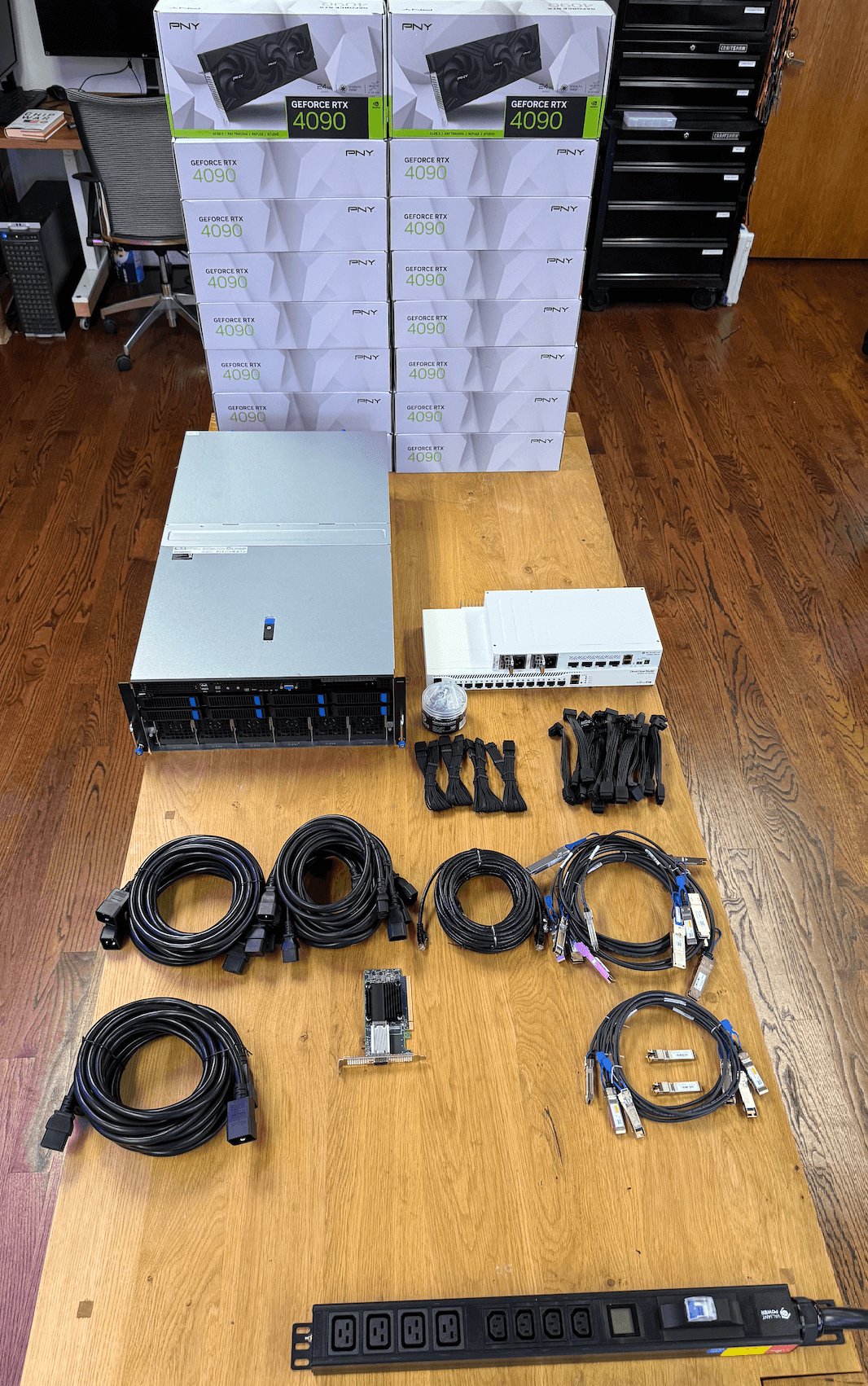
Building an Efficient GPU Server with NVIDIA GeForce RTX 4090s/5090s
Building an Efficient GPU Server with NVIDIA GeForce RTX 4090s/5090s
In today’s AI-driven world, the ability to train AI models locally and perform fast inference on GPUs at an optimal cost is more important than ever. [1] Building your own GPU server with an RTX 4090 or RTX 5090 — like the one described here — enables a high-performance eight-GPU setup running on PCIe 5.0 with full x16 lanes. [1] This configuration ensures maximum interconnect speed for all eight GPUs. [1] In contrast, most similar setups are limited by the PCIe bus version (such as PCIe 4.0 or even lower), due to the challenges of running longer PCIe extensions. [1]
This guide will walk you through our process of building a highly efficient GPU server using NVIDIA’s GeForce RTX 4090s. [1] We’ll be constructing two ...